
Ransomware Detection Techniques

Ransomware Detection - delete - decrypt - backup
Ransomware Detection
Ransomware Virus Removal and Pre-Detection. We are provide the data recovery services after Ransomware Virus Attack. Ransomware Detection – Ransomware Remove – Infected Data Decryption – Data Secure and Data Backup Techniques – Virus Solution Provider.


advance preparation against ransomware
Pre-Detection Ransomware
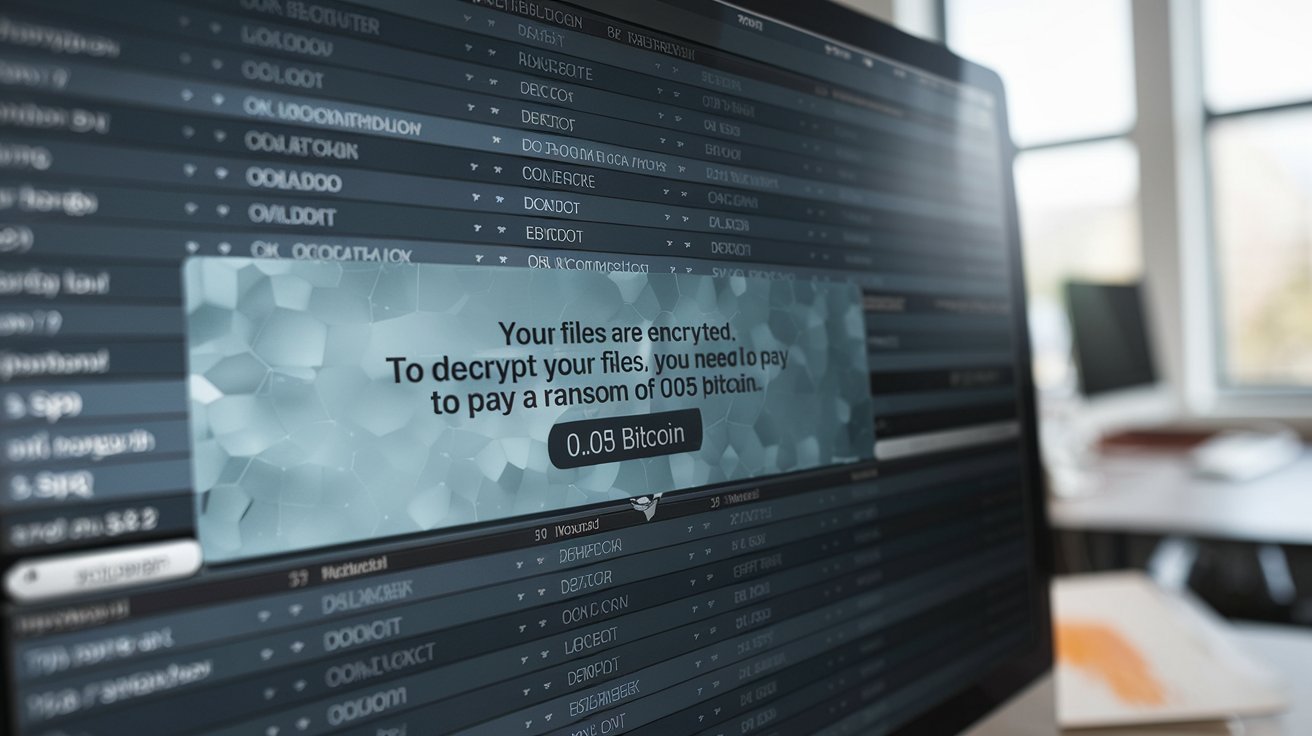
Ransomware detection is the process of identifying and detecting the presence of ransomware on a computer system. Similar to other types of malware, ransomware is specifically designed to infiltrate a computer system and operate covertly until its intended purpose is achieved. In the case of ransomware, the objective is for the victim to only become aware of the infection when they receive the ransom demand. To counteract this, anti-ransomware solutions are developed to detect the presence of ransomware at an earlier stage, ideally before any harm is done. These solutions employ various techniques for ransomware detection, aiming to overcome the stealth and defense evasion capabilities of ransomware.
Detecting a Cyber Attack Early is Crucial
The sooner an incident is discovered and resolved, the less opportunity the attacker has to steal sensitive data or harm the business. In the case of ransomware, early detection is even more critical. Ransomware can cause irreversible damage, especially if it encrypts data that isn’t backed up securely. Even if the victim pays the ransom, the encrypted data may remain irrecoverable. Therefore, it is essential to identify and eliminate the ransomware infection before encryption begins to minimize its impact.
With the evolution of ransomware, early detection has become increasingly important. Modern variants of ransomware often steal a company’s sensitive data before encrypting it. By detecting the ransomware before this data theft occurs, the company can avoid a costly and embarrassing data breach.
Types of Ransomware Detection Techniques
1. Signature-Based Detection:
This method involves identifying malware by comparing its signatures, such as file hashes, domain names, IP addresses of command and control infrastructure, and other unique indicators. Signature-based detection systems maintain a library of these signatures and compare them to incoming or running files to determine if they are malware. However, this method is becoming less effective as ransomware groups frequently create new variants that evade signature-based detection.
2. Behavior-Based Detection:
Behavioral detection algorithms can be used to identify ransomware by looking for specific malicious activities or anomalous behavior. Ransomware exhibits unusual behavior during its encryption stage, where it opens, reads, and overwrites multiple files with encrypted versions. Monitoring file operations or encryption activities can help detect this unusual behavior and alert anti-ransomware solutions.
3. Detection of Abnormal Traffic:
Ransomware can also be detected at the network level by monitoring for abnormal traffic patterns. Modern ransomware often steals and exfiltrates sensitive data before encrypting it, requiring large-scale data transfers from the network to external systems controlled by the attacker. While ransomware may attempt to conceal these transfers, they can still generate anomalous network traffic that can be traced back to the presence of ransomware on the system.
Recommended for You


Defeat Ransomware Attacks

Cylance Ransomware Attack and Data Recovery


Which is the Most Affordable Ransomware Data Recovery Services in Delhi?

Which is the Best Ransomware Data Recovery Services in Delhi?

Which is the Best Data Recovery Service in Delhi?

Which is the Most Affordable Ransomware Data Recovery Services?

Who Provides Professional Ransomware Data Recovery Services in Delhi?


Can Virus Solution Provider Recover Data from Laptop?

Who Provides Professional Computer Data Recovery Services?


Suggested, on your interest.

Review of Virus Solution Provider Computer Data Recovery Services

Review of Virus Solution Provider Hard Drive Data Recovery Services

Who Provides the Best Ransomware Data Recovery Services?

How to Recover Data from an Undetected SD Card?

Hassle-Free Ransomware Recovery: Why You Can Rely on Us

Business Data Locked by Ransomware? Get Immediate Recovery

Decrypt Makop Ransomware Data

Which is the Best Data Recovery Service in Delhi?

Can Virus Solution Provider Recover Data from Laptop?


Remove Black Panther Ransomware Virus and Recover Encrypted Data

